In today’s digital era, people are constantly reminded of the importance of protecting your data. Data breaches happen on a regular basis, and anyone can fall victim to it. This is a practical demonstration of a basic way that data is stolen, and how to protect against it.
For this project, I started up two virtual machines, and wrote a quick python program to have them communicate with each other using sockets.
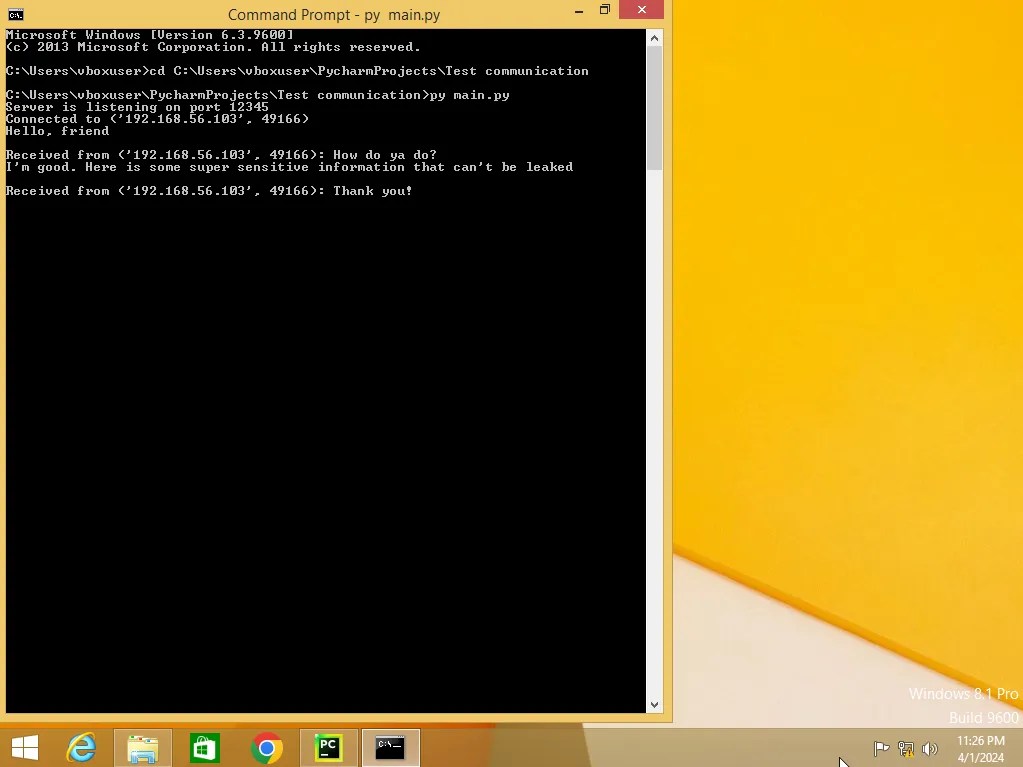
But there is a problem with the way these two machines are communicating. The messages are not encrypted. Anyone snooping on that network can peak in and see everything they are saying. To demonstrate this, I fired up another virtual machine, and ran a program called “Wireshark”, a popular packet analyzer.
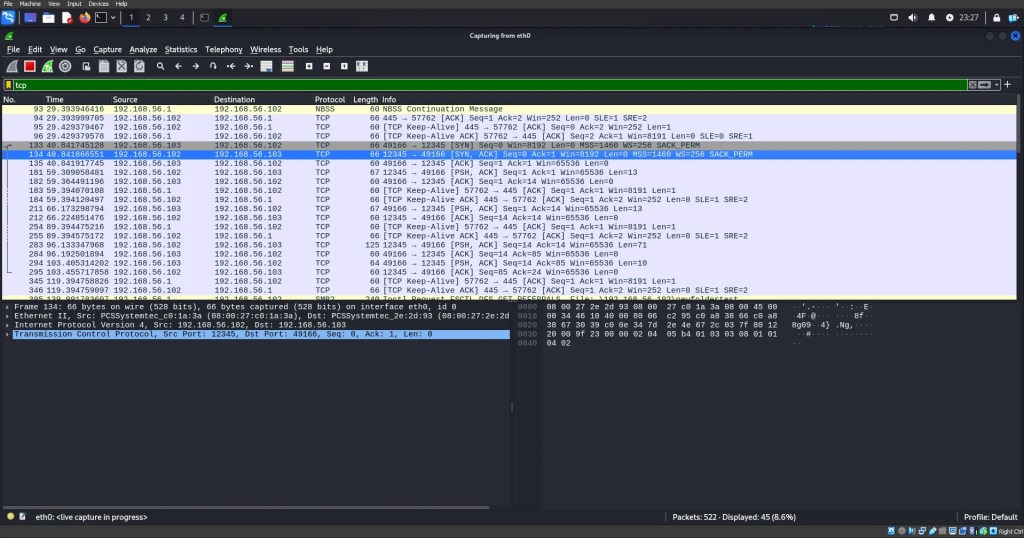
As you can see, by just setting the filter to tcp, I was able to exclusively view the traffic happening between these two virtual machines. In this data, I can easily see the exact messages they were sending to each other. It’s effortless.
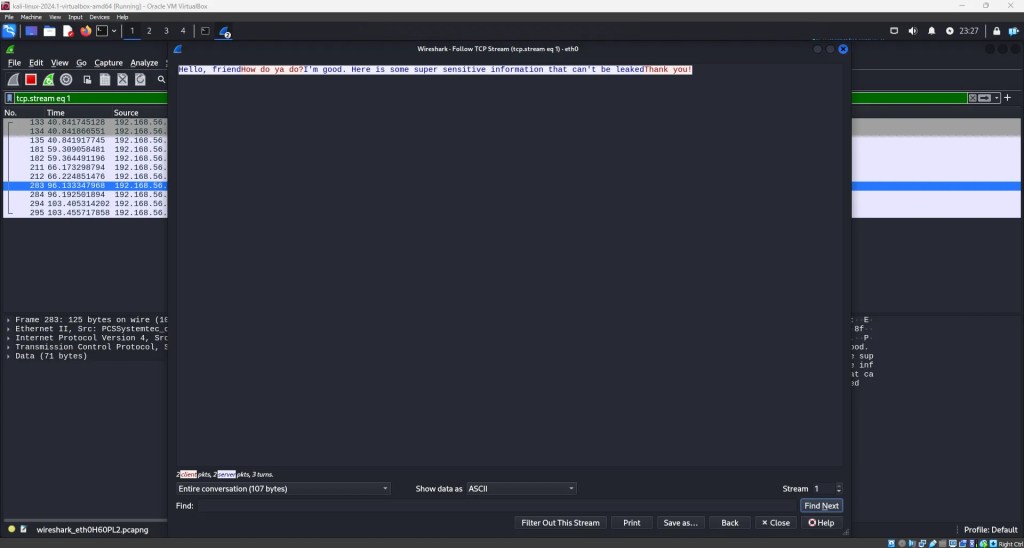
This is not something you want to happen if you are exchanging sensitive information. Luckily, there is an easy way to prevent this from happening. Data encryption. As a simple example, I’ll demonstrate a very weak encryption algorithm to do this before we move onto a more secure one. We will first encrypt the data with ROT-13 (simply rotating each character forward 13 characters in the alphabet). I coded up a simple ROT-13 encryption/decryption function in python here.
def encrypt_decrypt(message):
message = message.lower()
# Create variable to store the encrypted message
cipher = ""
# Loop through each character in message, rotating the character if it is an ascii letter
for x in message:
if x in string.ascii_letters:
i = 0
while x != string.ascii_letters[i]:
i += 1
cipher = cipher + string.ascii_letters[i + 13]
else:
cipher = cipher + x
# Print encrypted message
return cipher.lower()This can be added to the chat program to encrypt the messages before they are sent, and then unencrypt them once they have been received. So, now this is what we can expect to see.
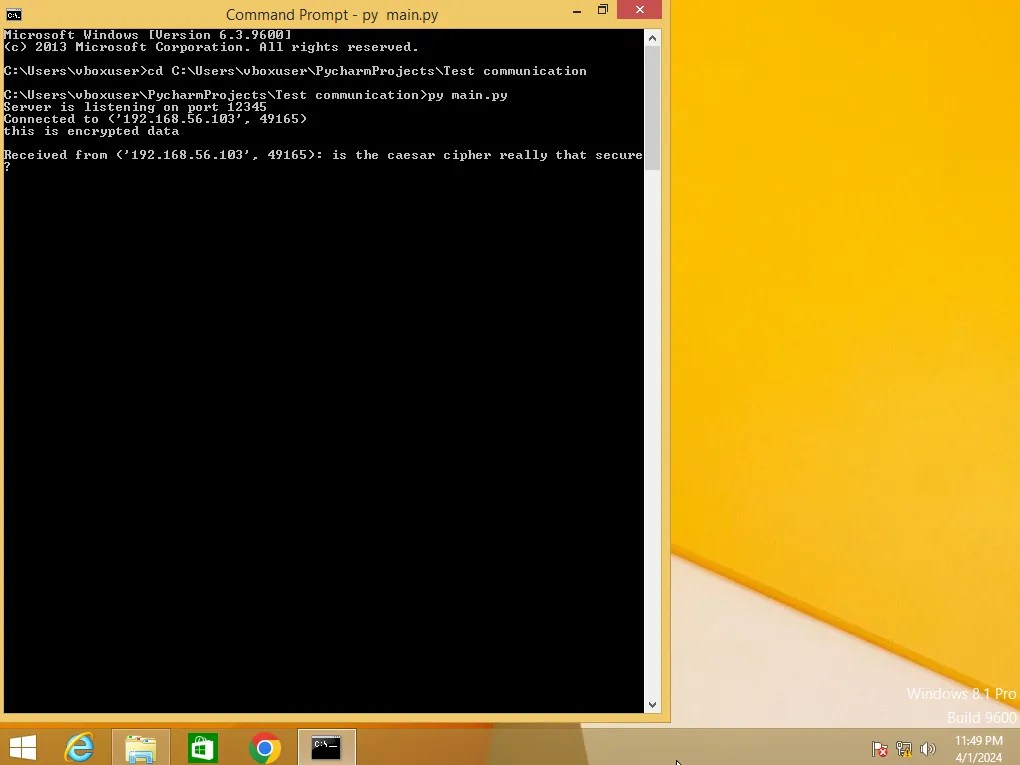
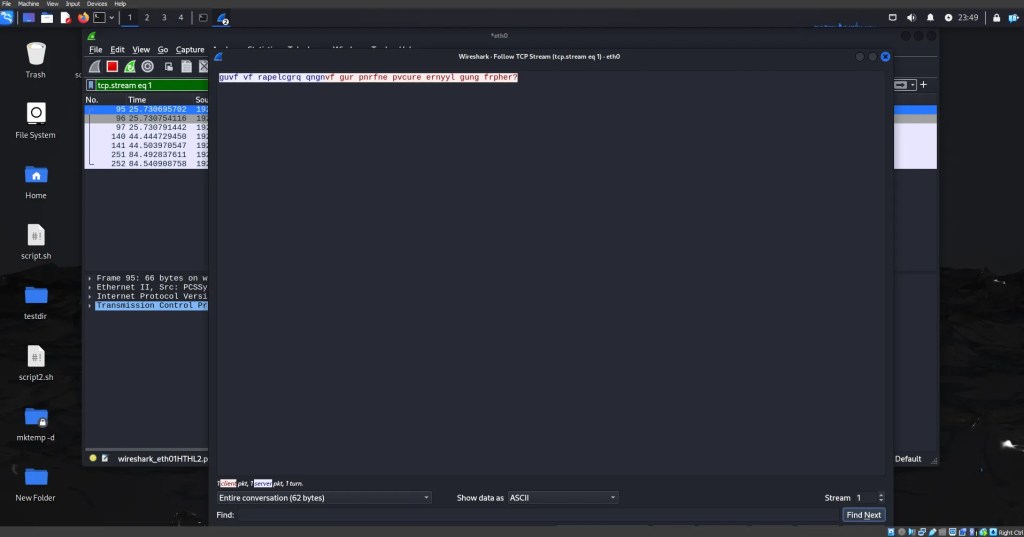
As you can see, the attacker intercepting the data will now see something that looks nonsensical. But… ROT-13 is an extremely simple, weak encryption algorithm. A child could break this encryption, so we are going to want to use something much stronger than this. A better option is to use AES-256. This is considered one of the strongest encryption algorithms. It is used by banks, the military, and other government entities. I won’t go too deep into exactly how AES is done right now. That is for another article. I will show you how to implement it into an application like this. I used python’s cryptodome library to code a function that encrypts and decrypts message using AES-256.
from Crypto.Cipher import AES
# encryption function
def encrypt256(message):
# initialize key, iv (which were initially randomly generated), and AES object
key = b'\xb1\x81\xc0\xe2\xa0N#\xd2F\xd3\xb3\xee\x07m\t\xb8r\xc4d"\xa5\xdbN\x0fD&\xea\x06\xbb\xd8\xbe\xdd'
iv = b'\x85\xb0\xf5\xc0\x19\x8f,)?\x90\xe0\x965TX\xe8'
cipher = AES.new(key, AES.MODE_CFB, iv)
# encrypt message
ciphertext = cipher.encrypt(message.encode('utf-8'))
# output ciphertext
return ciphertext
# decryption function
def decrypt256(message):
# retrieve key and ciphertext
key = b'\xb1\x81\xc0\xe2\xa0N#\xd2F\xd3\xb3\xee\x07m\t\xb8r\xc4d"\xa5\xdbN\x0fD&\xea\x06\xbb\xd8\xbe\xdd'
iv = b'\x85\xb0\xf5\xc0\x19\x8f,)?\x90\xe0\x965TX\xe8'
# declare AES object and decrypt message
cipher = AES.new(key, AES.MODE_CFB, iv)
plaintext = cipher.decrypt(message)
# output plaintext
return plaintext.decode('utf-8')This is a simulated scenario, so the way this is programmed is in a bit of a simplified manner, but in a real scenario you would want the key and iv to be randomly generated each time. AES is basically unbreakable by today’s standards, but if the encryption key is compromised, then the data is no longer safe.
After implementing these functions into the chat program, this is what we will see.
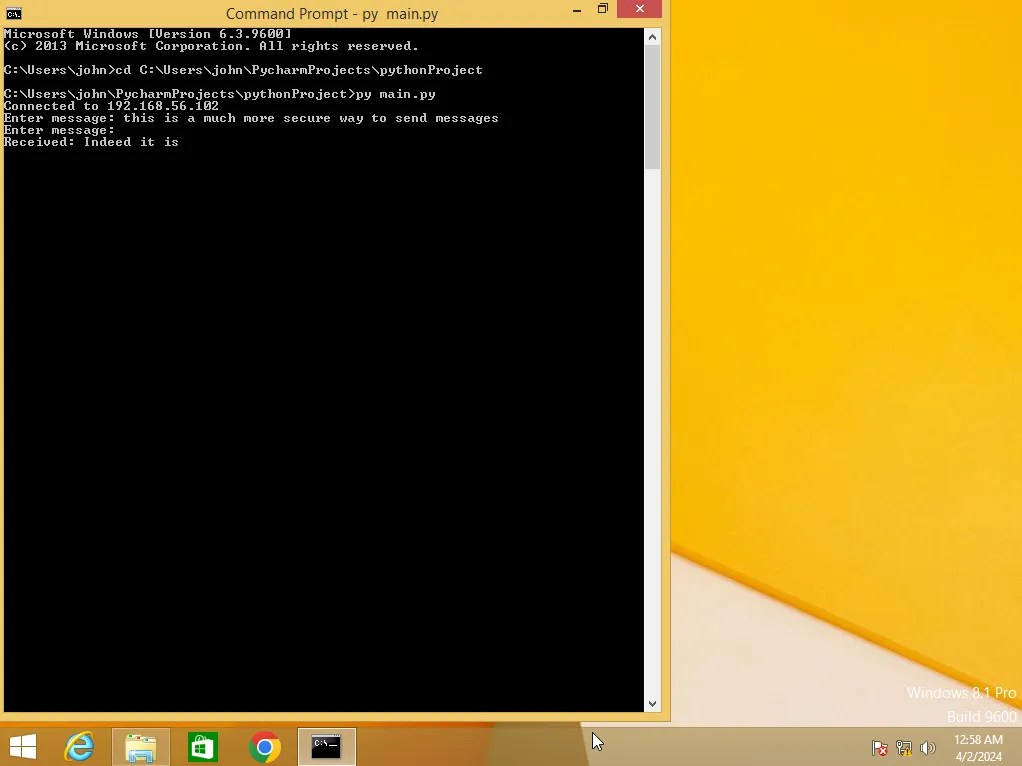
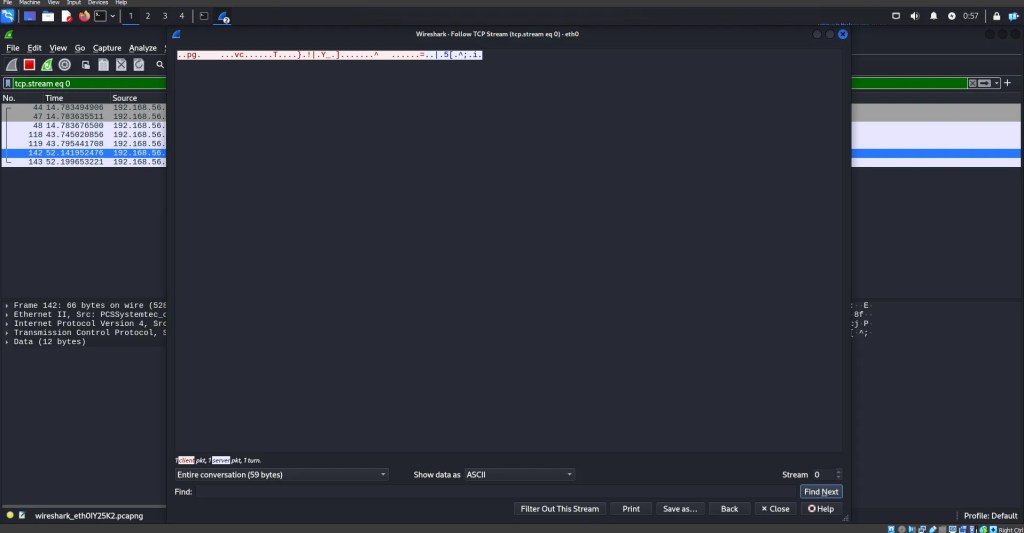
As you can see here, the machines chatting with each other can see the messages just fine, but the attacker snooping in with Wireshark is left totally in the dark trying to decipher gibberish.
If you want to take a look at some more types of encryption, I have created a Github repository with a program I am currently developing that allows the user to use several modern encryption algorithms. At the time of writing this it includes AES, Least Significant Bit Steganography, and hash cracking capabilities. More to come.
I also have a GitHub repository that has a program I wrote that features many different types of historical cryptographic algorithms, if you’re interested in learning about those. That one includes the Vigenere Cipher, Playfair Cipher, Columnar Transposition Cipher, and many more.
Modern Encryption Repo: https://github.com/ericw317/ModernEncryption
Historical Encryption Repo: https://github.com/ericw317/Cipher


Leave a comment