Table of Contents
Introduction
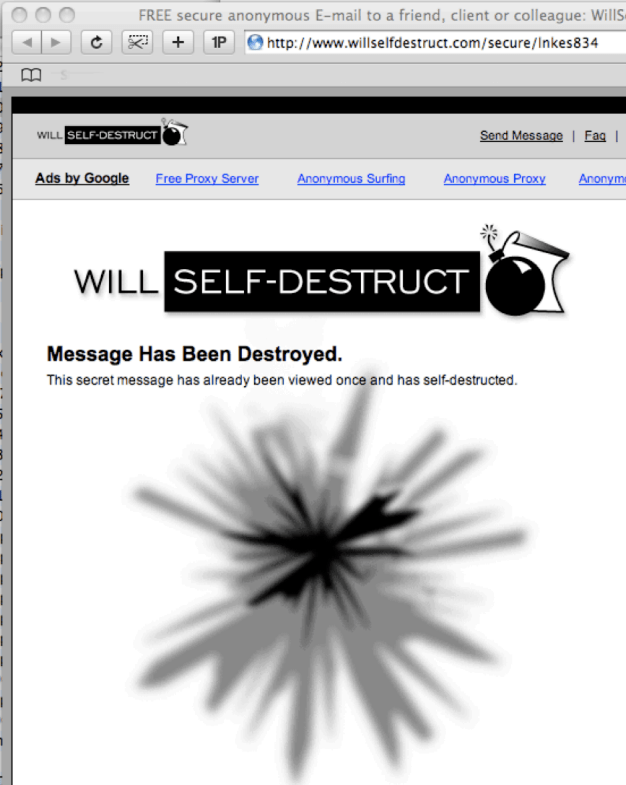
This is a write-up for a scenario that was posted on the Digital Corpora website. The scenario details an incident from the Summer of 2008 that occurred at a fictitious university called Nitroba State University. A teacher in the Chemistry department named Lily Tuckrige has been receiving harassing e-mails that she suspects are being sent by a student in her class. After Tuckrige reported this incident to the IT department, they investigated the e-mail header to discover that the message originated from a Nitroba student dorm room shared by three women. Nitroba provides an Ethernet connection in every dorm room, but not Wi-Fi access, so one of the women’s friends installed a Wi-Fi router in the room with no password. To further investigate, the IT department placed a network sniffer on the ethernet port. On July 21st, Lily Tuckrige received another harassing e-mail; however, this time the perpetrator sent it using a website called “willselfdestruct.com”. This website briefly displays the message to the recipient, then deletes the message. My objective is to analyze the network capture obtained from the network to determine who sent the harassing message to Lily Tuckrige.
Evidence Examined
| Date Acquired | Source Name | Source Description |
| 10/29/2024 | nitroba.pcap | Network capture of Nitroba University network |
Hash values
Nitroba.pcap Source:
MD5 – 9981827f11968773ff815e39f5458ec8
SHA1 – 65656392412add15f93f8585197a8998aaeb50a1
Nitroba.pcap Acquisition:
MD5 – 9981827f11968773ff815e39f5458ec8
SHA1 – 65656392412add15f93f8585197a8998aaeb50a1
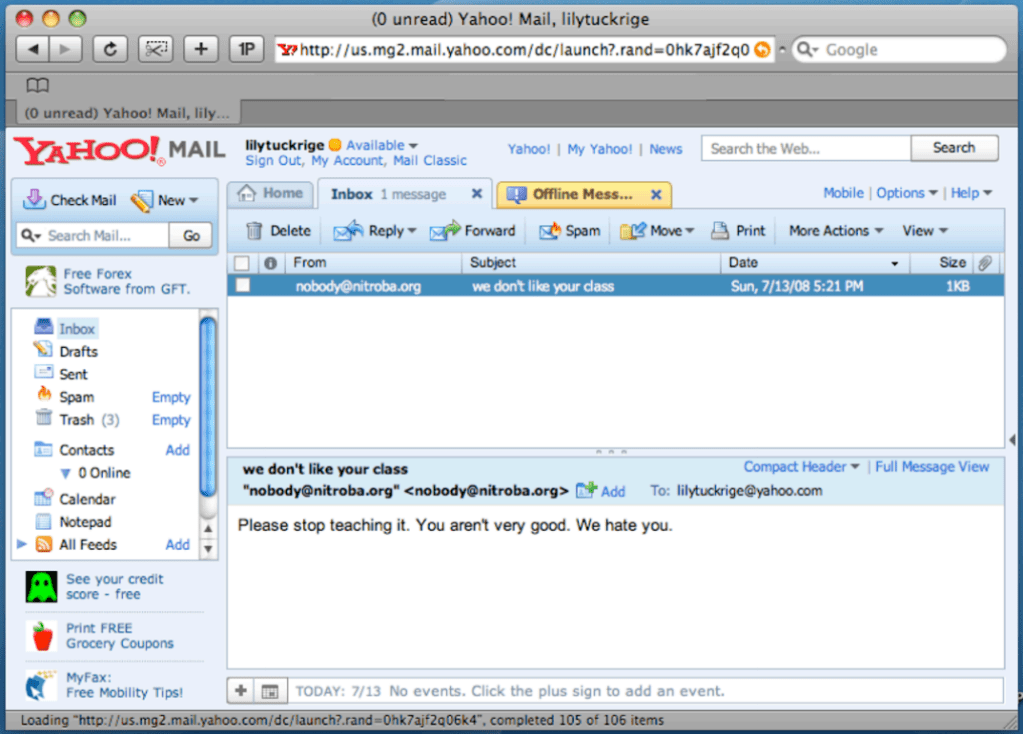
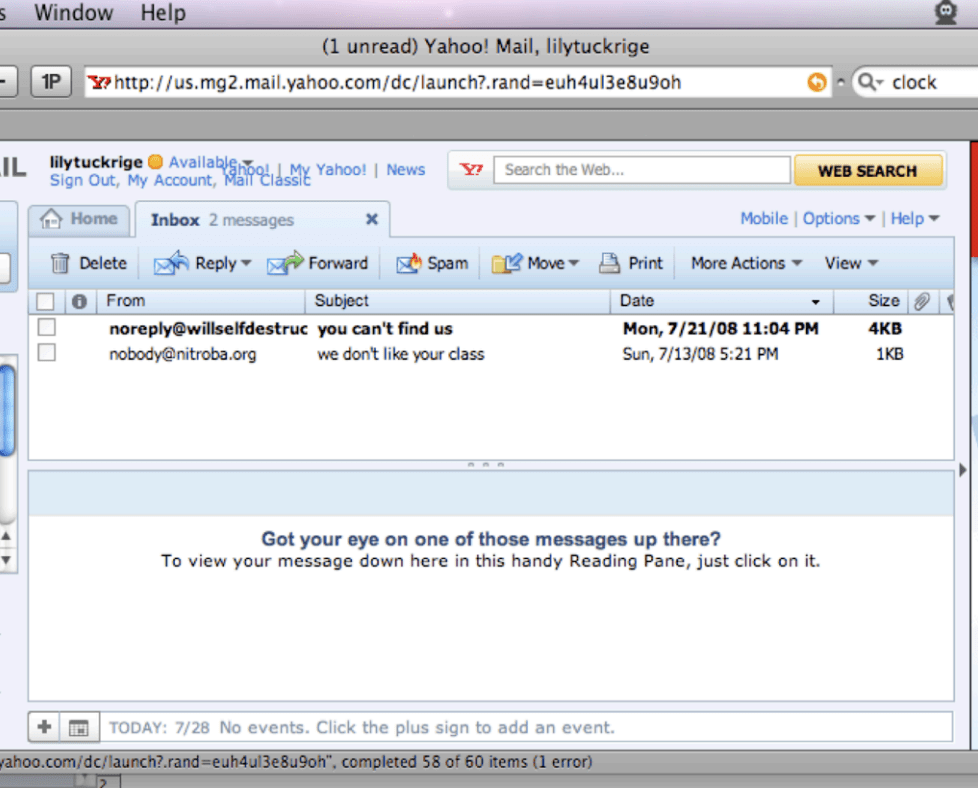
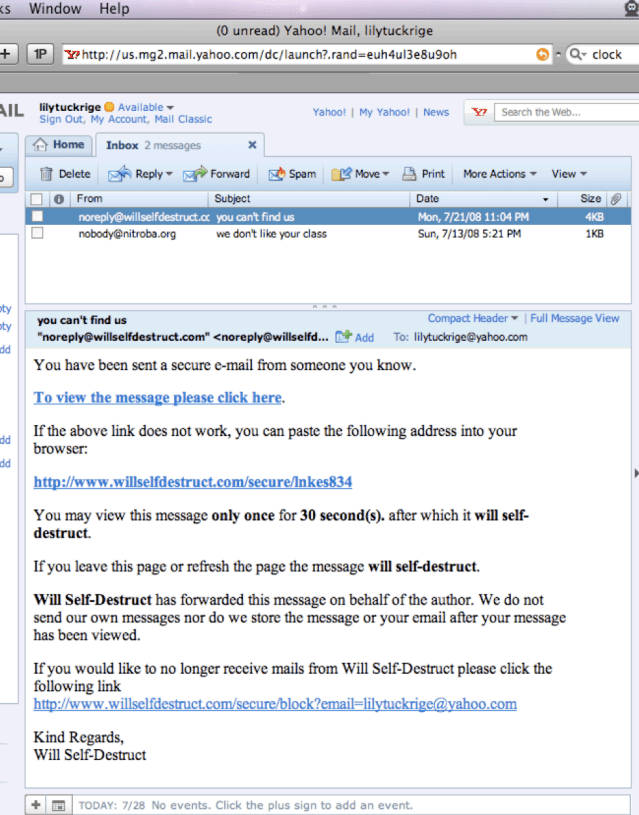
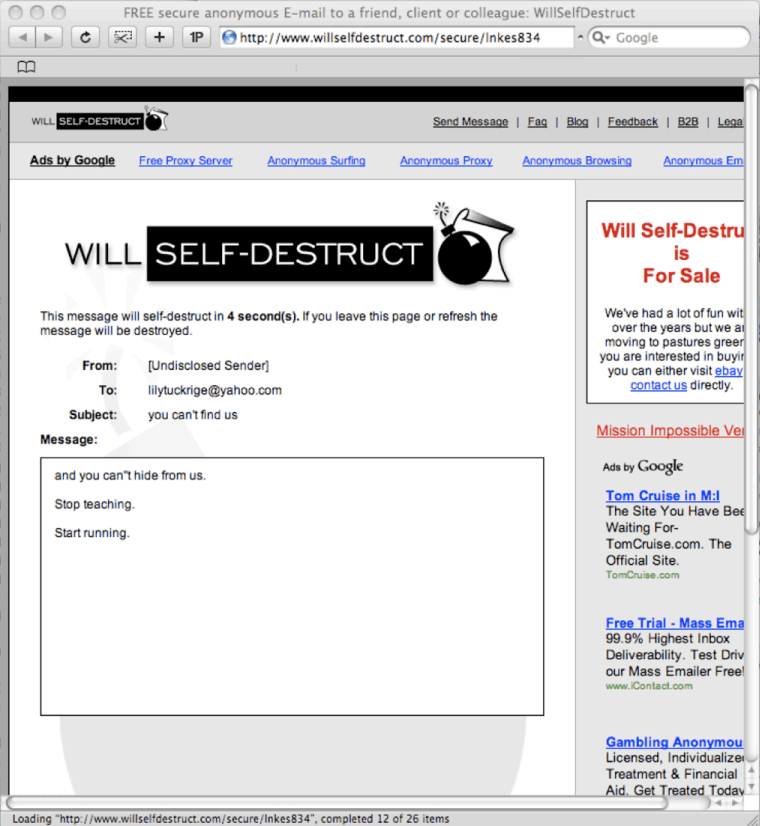
E-mails sent to Lily Tuckrige:
Lily Tuckrige Chemistry Class List:
Students:
Amy Smith
Burt Greedom
Tuck Gorge
Ava Book
Johnny Coach
Jeremy Ledvkin
Nancy Colburne
Tamara Perkins
Esther Pringle
Asar Misrad
Jenny Kant
Summary
The evidence shows that Johnny Coach is the student that sent the harassing e-mails to Lily Tuckrige. My conclusion is based on the fact that the internal IP address and MAC address responsible for sending multiple harassing e-mails to Lily Tuckrige is strongly linked to a Gmail account that belongs to Johnny Coach.
Detailed Findings
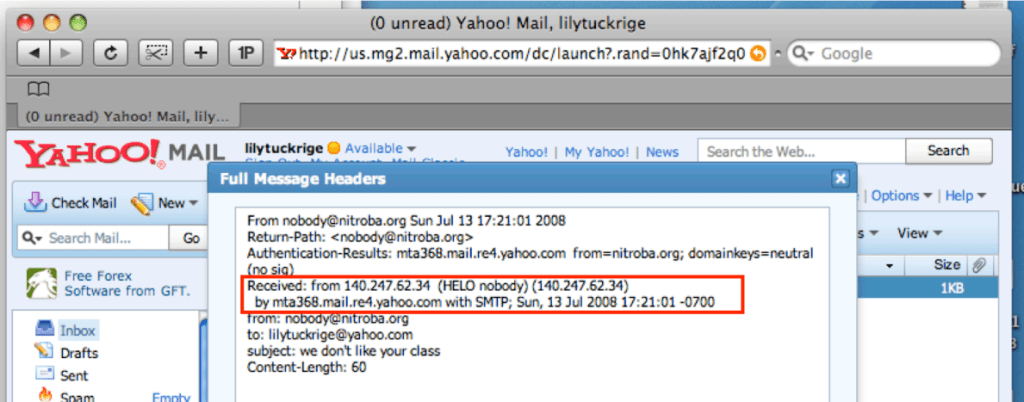
I started my analysis by examining the public IP address that sent an inappropriate e-mail to Lily Tuckrige on July 13, 2008. This information can be found in the e-mail header that Lily Tuckrige provided. E-mail headers contain metadata that tracks the journey an e-mail made from its source to its destination. This metadata contains things like the sender address, recipient address, server details, and timestamps. In the “Received” portion of an e-mail header, you can see where an e-mail was sent from, and where it arrived. The screenshot below, provided by Lily Tuckrige, shows that the harassing e-mail sent to her on July 13, 2008, was sent to a yahoo.com mail server from the IP address. 140.247.62.34.
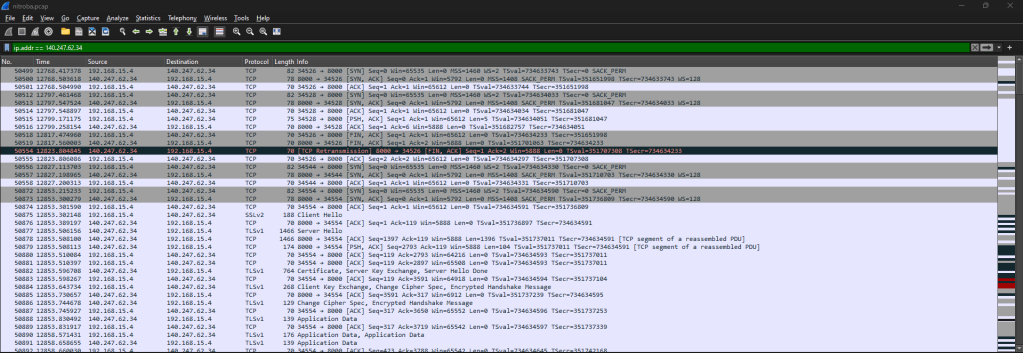
As mentioned in the Introduction, the IT department at Nitroba University confirmed that this IP address belongs to a Nitroba dorm room. This dorm room is connected to the internet through an Ethernet connection, but there has also been a Wi-Fi router installed that is not password-protected. This means that the IP address we see above (140.247.62.34) is just the public IP address that is assigned to anyone who connects to that Wi-Fi router. So, this alone only tells us which network it came from, but not who specifically sent the e-mail. Anyone who connects to this network is assigned an internal IP address unique to their device on the network, so the router can route relevant traffic to their device. In order to find the internal IP address, we need to dig a bit deeper. So I narrowed my search by analyzing the network capture (nitroba.pcap file) with a software called Wireshark. Wireshark is a software that can capture and analyze network traffic. Using this, I was able to search for specific data within the nitroba.pcap capture. I started by using the command “ip.addr == 140.247.62.34” to search for all traffic going to and from the IP address, “140.247.62.34”. After using this filter, it became clear that most of the communication happening on this IP was coming from the internal IP address, “192.168.15.4”.
Now that I had this internal IP address to look into, I decided to filter with the command “ip.addr == 192.168.15.4 and frame contains ‘tuckrige’”. This command will filter all traffic going to and from the IP “192.168.15.4” where the packet data contains the term “tuckrige”. From here, I was able to see three packets.
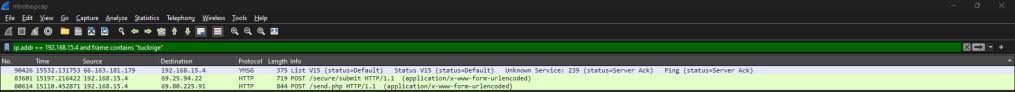
Two of these packets used the HTTP protocol. This is a common protocol used to send data over the web. In modern times, most data is transferred using HTTPS, which encrypts data during transit so that it cannot be read until it reaches its destination. Conveniently, these packets were sent using HTTP, which is unencrypted, allowing us to view the data in plaintext. The data in one of these packets shows an e-mail sent from “sendanonymousemail.net” using the web browser, Mozilla Firefox. The e-mail was sent to “lilytuckrige@yahoo.com” from “the_whole_world_is_watching@nitroba.org”. The subject read, “Your class stinks” and the message read, “Why do you persist in teaching a boring class. We don’t like it. We don’t like you.” The data in the other packet shows another e-mail also sent using the Firefox browser. This one shows that it was sent from “willselfdestruct.com”, and from the content of the message we can see that it is the same harassing e-mail that Lily Tuckrige provided in the “Evidence Examined” section of this report.
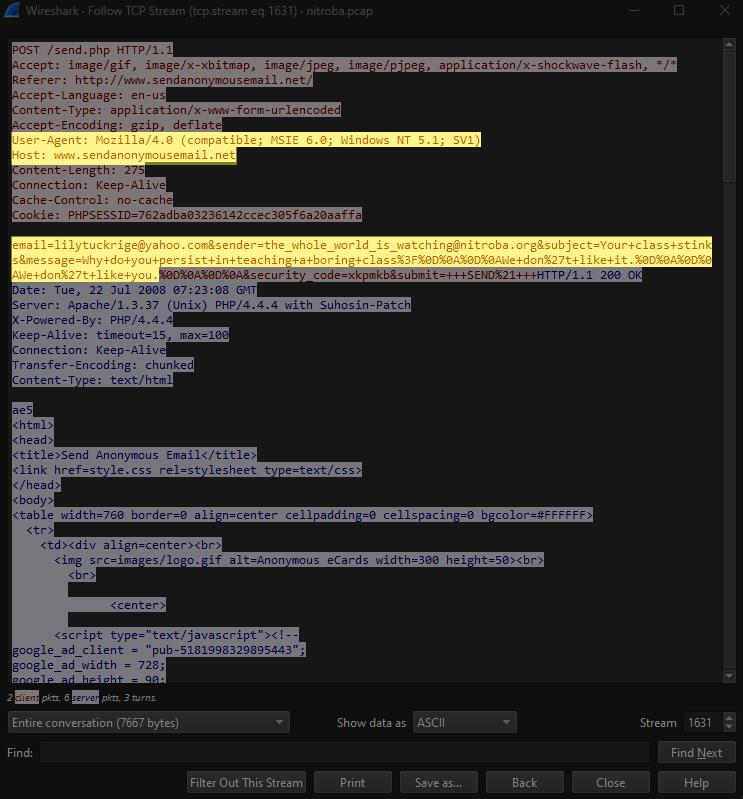
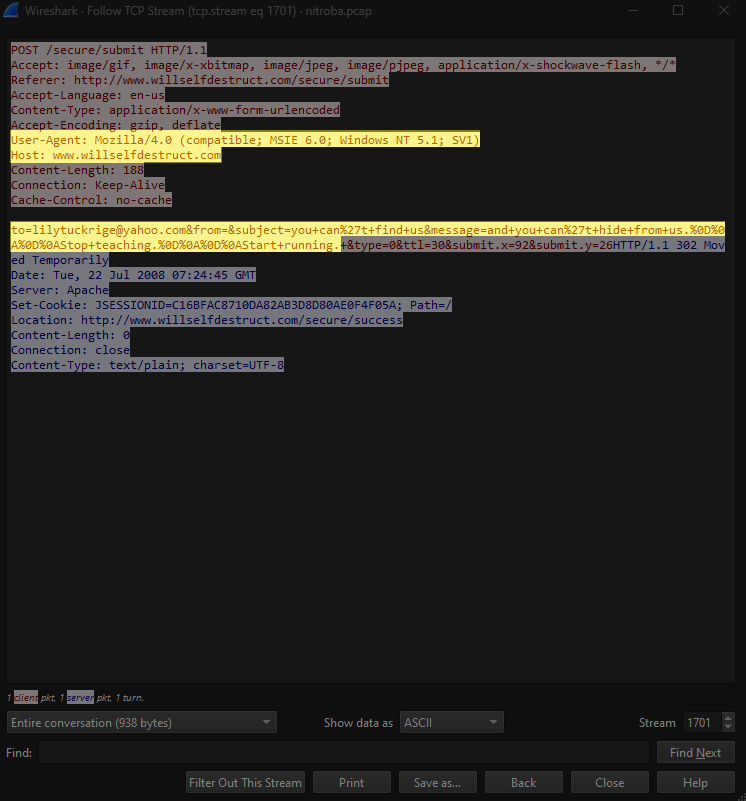
This confirms that the internal IP address, “192.168.15.4” did send the harassing e-mail to Lily Tuckrige, but we still need a bit more data before we can come to a conclusion. The internal IP address will not always belong to the same device. When a device connects to a network, it is temporarily assigned an internal IP address based on what is available. But if that device were to disconnect from the network, and then a different device connects to the network, then that different device could be assigned that same internal IP address. So, we need to connect this message to a physical device. We can do this through the MAC address. A MAC address is a unique identifier assigned directly to a physical device. The MAC address is stored directly on the device’s NIC (network interface controller) and is something that is permanently tied to that device, regardless of which network it connects to. Luckily, Wireshark also provides us with the MAC address of the device that sent this data. The screenshot below shows that the MAC address is “00:17:f2:e2:c0:ce”.

Now that we know the internal IP address and MAC address of the device that sent the harassing e-mails to Lily Tuckrige, all that is left to do is identify which student this device belongs to. To do this, I used the Wireshark command, “filter by 192.168.15.4 and frame contains ‘mail’ and http”. This command filters all traffic from the IP address “192.168.15.4” with packets containing the term “mail”. The final part of the command will ensure that the output is also filtered to only show packets using the HTTP protocol so we can read unencrypted data. After looking through this data, I was able to find a packet with data accessing Google calendar and Gmail, each with a cookie pair containing the e-mail address, “jcoachj@gmail.com”.
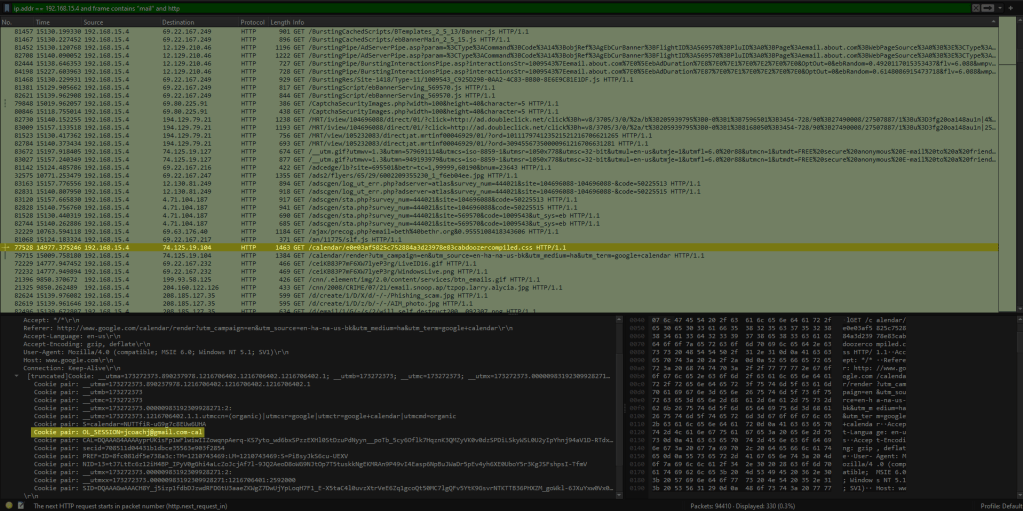
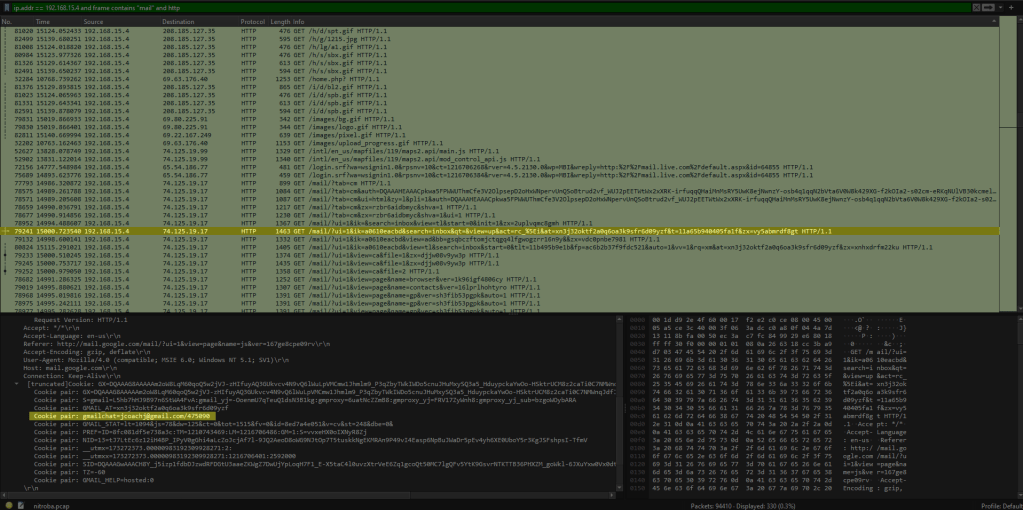
If we look at the MAC address of each of these packets, we can see that it indeed matches the MAC address of the sender of the harassing e-mails from earlier.

We can establish that the e-mail “jcoachj@gmail.com” belongs to Johnny Coach, based on the list of students provided in the “Evidence Examined” section, which strongly suggests that Johnny Coach is the one who sent the harassing e-mails to Lily Tuckrige.
Conclusion
Based on the findings from analyzing the network traffic using Wireshark, we can see that the device with the MAC address “00:17:f2:e2:c0:ce” sent the harassing e-mails to Lily Tuckrige. This same device also connected to Google services multiple times with a cookie pair displaying the e-mail address, “jcoachj@gmail.com”. Correlating this e-mail with the student list in the “Evidence Examined” section, it becomes clear that the sender of the harassing e-mails is Johnny Coach.


Leave a comment