What is SQL Injection?
SQL Injection is a security vulnerability that exists when an input field on a web page interacting with an SQL database fails to properly sanitize the input. This allows the attacker to exploit this vulnerability by injecting malicious SQL code, tricking the server into executing arbitrary queries.
Demonstration
This write-up will demonstrate a basic SQL Injection attack through a lab on HackTheBox called “Appointment”. This lab presents us with a login page that is vulnerable to SQL Injection.
The SQL query that this webpage uses to authenticate users likely looks something like this:
SELECT * FROM users WHERE username = 'input_username' AND password = 'input_password';
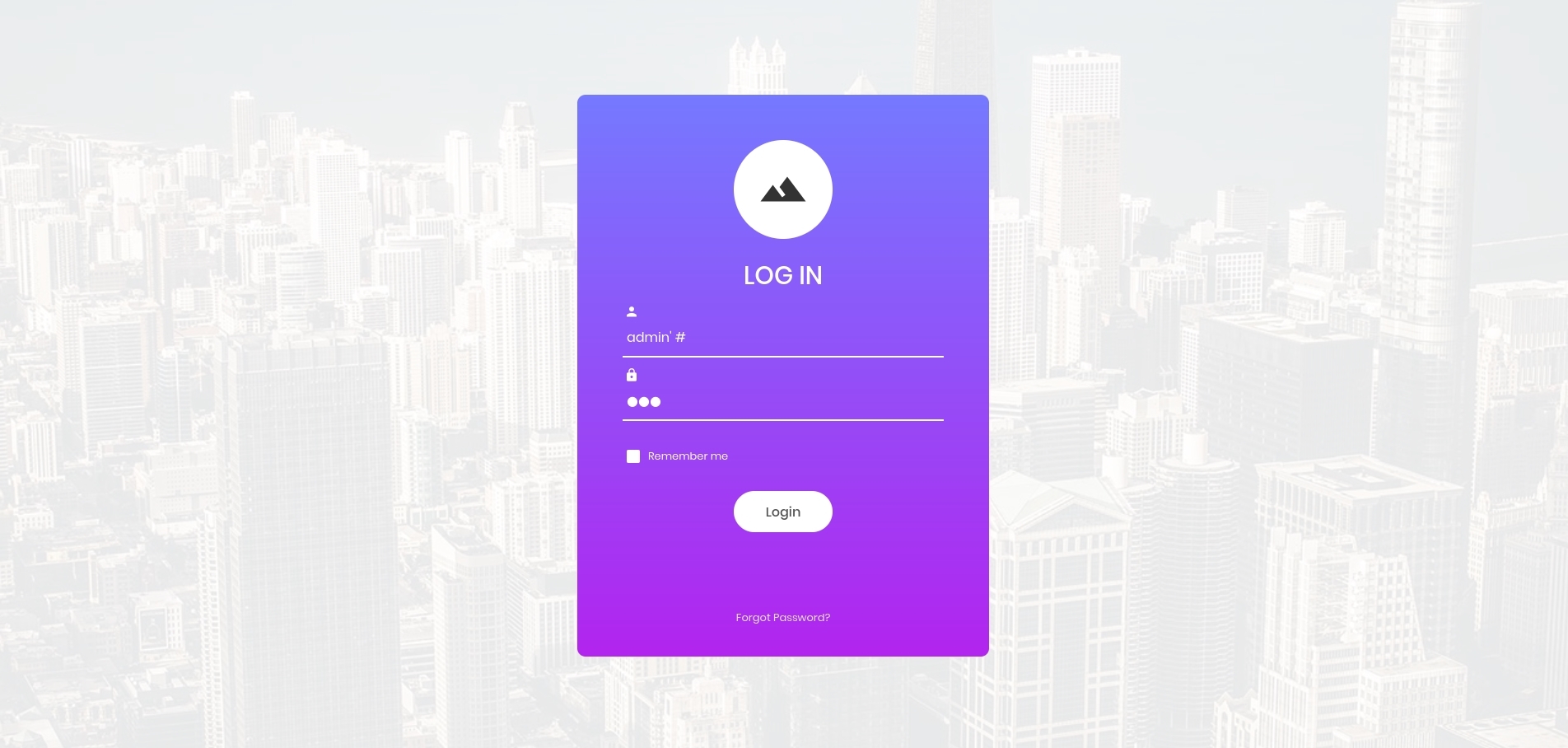
Because the input is not properly sanitized, we can craft an input in the username field to comment out the rest of the query after ‘input_username’. This can be achieved by entering the following in the username field:
admin' #
We enter “admin”, because that is the user we want to login as. We then enter the apostrophe to close off the quotation mark so that the rest of our query will be interpreted as code and not as the username string. Finally, we enter the “#”, which is the comment character in SQL (in some versions of SQL, you will need to use “–” as the comment characters instead of “#”), which will essentially make the server ignore everything in the query from that point forward. So the new statement will now look like this:
SELECT * FROM users WHERE username = 'admin' #' AND password = 'input_password';
Because everything from the “#” forward is ignored, the server will actually be reading the query as this:
SELECT * FROM users WHERE username = 'admin'
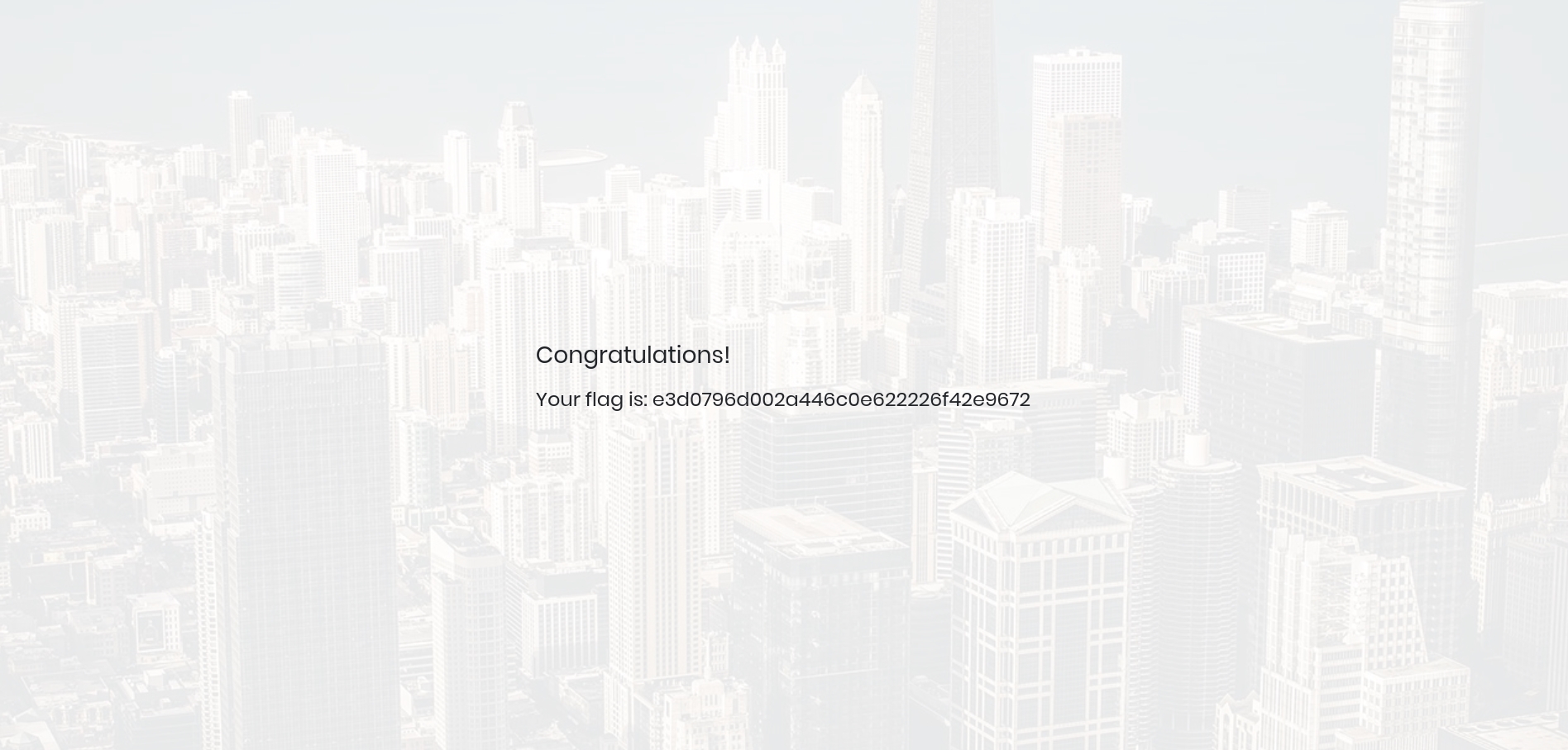
This will bypass the password field altogether and just log us in as “admin”. We do still need to enter a password though (which can be whatever you want), since the server probably checks to see if that field is empty or not before running the authentication process. But once we click “Login”, the password will not actually be checked, so it doesn’t matter what you enter as the password.

Leave a comment